Recreating and Researching Phishing Techniques
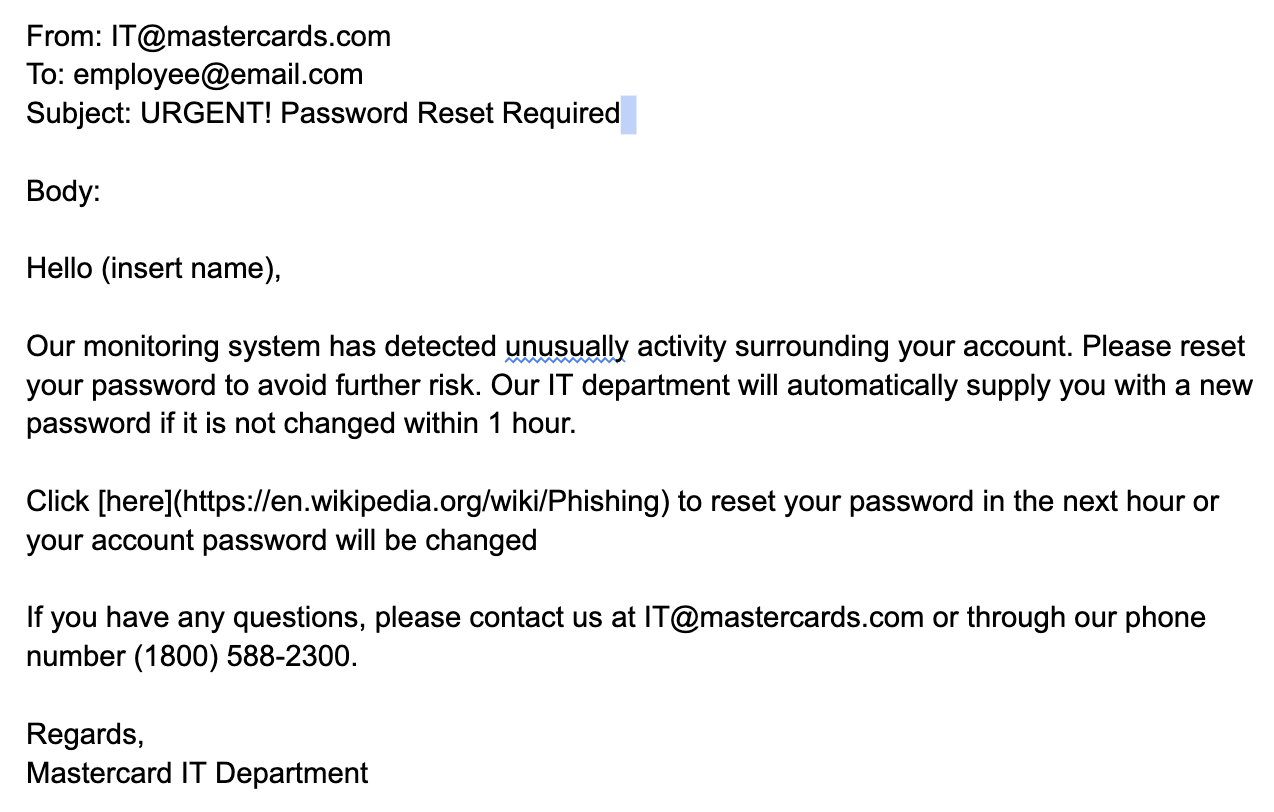
The job simulation opened up with one of the most basic and common social engineering techniques: phishing. Using emails as the medium, I explored different ways attackers try to extract personal information from their victims.
The first assignment was to locate anything suspicious in a phishing attempt and improve upon the attempt. I tried following the original prompt of an account termination to play on to the victims fears and push urgency. I fixed basic spelling errors and hid the link using embedded texts.
The more I went through the job simulation, the more I learned about other techniques threat actors use when crafting a malicious email, such as adding context to make the email slightly more believable or sprinkling in details specific to the company to add legitimacy.
I put all the knowledge I gained into a Google Slides presentation on how to avoid falling for these phishing attempts and keep your personal information safe.